

i user privacy.com. it hits my account with unique names per card. so easy to line up.
Nope. I don’t talk about myself like that.


i user privacy.com. it hits my account with unique names per card. so easy to line up.


None of this has anything to do with root on my machine though.
But it does. If your machine is compromised, and they have root permissions to run whatever they want, it doesn’t matter how segmented everything is, you said yourself you jump between them (though rare).
Security Configuration Assessment
SCA is for payment services, no? I’m in the US, and this seems to be an EU thing I’m not very familiar with, but regardless, we don’t touch ecommerce at all, we’re B2B and all payments go through invoices.
No, it’s just a term for a defined check that configurations meet a standard. An SCA can be configured to check on any particular configuration change.
Also, that should be painfully obvious because you wouldn’t get reporting updates, no?
Not necessarily? Hard to tell if something is disabled vs just off.
If you’re worried someone will disable your tools, why would you hire them in the first place?
I don’t hire people… especially people in other departments.
But while I found this discussion fun, I have to get back to work at this point. Shit just came up with a vendor we used for our old archaic code that might accelerate a rust-rewrite… and logically related to the conversation I might be in the market for some rust devs.


And this, right here, is my problem with a lot of C-suite level IT policy, it’s often more about CYA and less about actual security.
Remediation after an attack happens is part of the security posture. How does the company recover and continue to operate is a vital part of security incident planning. The CYA aspect of it comes from the legal side of that planning. You can take every best practice ever, but if something happens. Then what does the company do if it doesn’t have insurance fallback or other protections? Even a minor data breach can cause all sorts of legal troubles to crop up, even ignoring a litigious user-base. Having the policies satisfied keeps those protections in place. Keeps the company operating, even when an honest mistake causes a significant problem. Unfortunately it’s a required evil.
A casual drive-by attacker won’t get much beyond whatever is cached on my system, and compromising root wouldn’t get much more.
On a company computer? That’s presumably on a company network? Able to talk and communicate with all the company infrastructure? You seem to be specifically narrowing the scope to just your machine, when a compromised machine talks to way more than just the shit on the local machine. With a root jump-host on a network, I can get a lot more than just what’s cached on your system.
I discovered that IT didn’t use MS or Google for their cloud stuff,
We don’t use google at all if it’s at all possible to get away with it… We do have disposable docker images that can be spun up in the VDI interface to do things like test the web side of the program in a chrome browser (and Brave, chromium, edge, vivaldi, etc…). We do use MS for email (and by extension other office suite stuff cause it’s in the license, teams… as much as I fucking hate what they do to the GUI/app every other fucking month… is useful to communicate with other companies… as we often have to get on calls with API teams from other companies), but that’s it and nextcloud/libreoffice is the actual company storage for “cloud”-like functions… and there’s backup local mail host infrastructure laying in wait for the day that MS inevitably fucks up their product more than I’m willing to deal with their shenanigans as far as O365 mail goes.
I’m considering moving to MicroOS as well, for even better security and ease of maintenance.
I’m pushing for a rewrite out of an archaic 80’s language (probably why compile times suck for us in general) into Rust and running it on alpine to get rid of the need for windows server all together from our infrastructure… and for the low maintenance value of a tiny linux distro. I’m not particularly on the SUSE boat… just because it’s never come up. I float more on the arch side of linux personally, and debian for production stuff typically. Most of our standalone products/infrastructure are already on debian/alpine containers. Every year I’ve been here I’ve pushed hard to get rid of more and more, and it’s been huge as far as stability and security goes for the company overall.
“even devs use standard IT images”
No, it’s “even devs meet SCA”. Not necessarily a standard image. I pointed it out, but only in passing. I can spawn an SCA for many different linux os’s that enforce/prove a minimum security posture for the company overall. I honestly wouldn’t care what you did with the system outside of not having root and meeting the SCA personally. Most of our policy is effectively that but in nicer terms for auditing people. The root restriction is simply so that you can’t disable the tools that prove the audit, and by extension that I know as the guy ultimately in charge of the security posture, that we’ve done everything reasonable to keep security above industry standard.
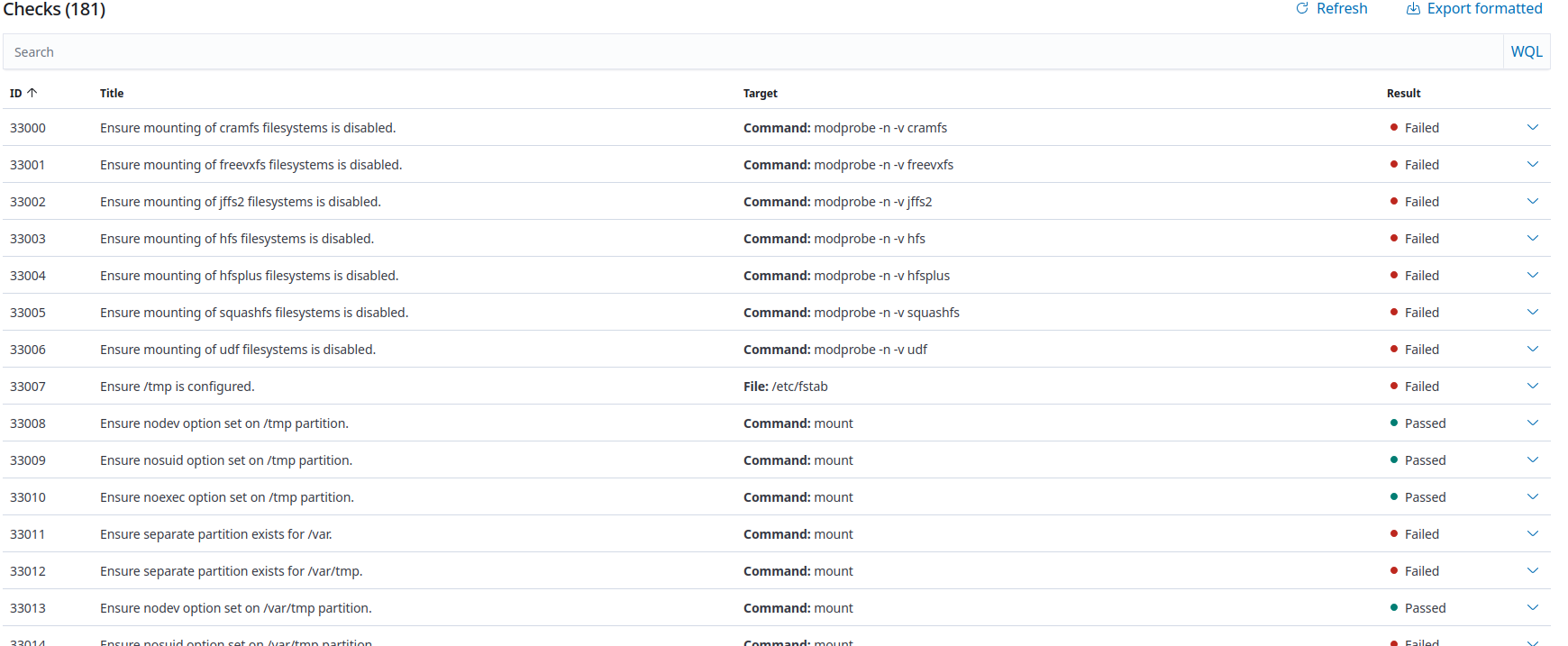
The SCA checks for configuration hardening in most cases. That same Debian example I posted above, here’s a snippet of the checks


No. I wouldn’t. Because minimum wage varies wherever you are in the USA. Where I live it’s over $13, nearly double. It would be disingenuous to claim 7.25 when literally nobody I know is at that rate.
That’s my point. Stop pushing the shit narrative. Statistically, you don’t know a single soul that’s at 7.25 either. Comparing the UK minimum wage, a country with 1/5th the population and 1/40th the landmass… Acting like the all of the USA is a monolith like the UK is disingenuous.


Because those states are small population wise, any attempt to push 7.25 as “normal” on an international forum is disingenuous. treating an issues that is distinct on a state hy state issue as if the federal is the end all be all is a lie of omission. Those same 21 states also have a lower cost of living.


I’m no expert on the process, but I’m pretty sure as long as the process server can attest that the papers were produced to the person being summoned. You don’t have to read it at all… The process server can just drop them in front of you and say “You’ve been served”.
I know that if you can’t be found alternate mechanisms exists, but usually requires attempting to exhaust all other avenues.
But the dude literally outright told the news he knows about it. I’m pretty sure that would be more than sufficient for the court to state that whatever mechanism they used to serve him was sufficient since he knew about it.


Eh, him going on the news talking about it will likely stand as evidence that he knows he’s being summoned.


I get your points. But we simply wouldn’t get along at all. Even though I’d be able to provide every tool you could possibly want in a secure, policy meeting way, and probably long before you actually ever needed it.
but I hate debugging build and runtime issues remotely. There’s always something that remote system is missing that I need
If the remote system is a dev system… it should never be missing anything. So if something’s missing… Then there’s already a disconnect. Also, if you’re debugging runtime issues, you’d want faster compile time anyway. So not sure why your “monolith” comment is even relevant. If it takes you 10 compiles to figure the problem out fully, and you end up compiling 5 minutes quicker on the remote system due to it not being a mobile chip in a shit laptop (that’s already setup to run dev anyway). Then you’re saving time to actually do coding. But to you that’s an “inconvenience” because you need root for some reason.
but my point here is that security should be everyone’s concern, not just a team who locks down your device so you can’t screw the things up.
No. At least not in the sense you present it. It’s not just locking down your device that you can’t screw it up. It’s so that you’re never a single point of failure. You’re not advocating for “Everyone looking out for the team”. You’re advocated that everyone should just cave and cater to your whim, rest of the team be damned. Where your whim is a direct data security risk. This is what the audit body will identify at audit time, and likely an ultimatum will occur for the company when it’s identified, fix the problem (lock down the machine to the policy standards or remove your access outright which would likely mean firing you since your job requires access) or certification will not be renewed. And if insurance has to kick in, and it’s found that you were “special” they’ll very easily deny the whole claim stating that the company was willfully negligent. You are not special enough. I’m not special enough, even as the C-suite officer in charge of it. The policies keep you safe just as much as it keeps the company safe. You follow it, the company posture overall is better. You follow it, and if something goes wrong you can point at policy and say “I followed the rules”. Root access to a company machine because you think you might one day need to install something on it is a cop out answer, tools that you use don’t change all that often that 2 day wait for the IT team to respond (your scenario) would only happen once in how many days of working for the company? It only takes one sudo command to install something compromised and bringing the device on campus or on the SDN (which you wouldn’t be able to access on your own install anyway… So not going to be able to do work regardless, or connect to dev machines at all)
Edit to add:
Users can’t even install an alternative browser, which is why our devs only support Chrome (our users are all corporate customers).
We’re the same! But… it’s Firefox… If you want to use alternate browsers while in our network, you’re using the VDI which spins up a disposable container of a number of different options. But none of them are persistent. In our case, catering to chrome means potentially using non-standard chrome specific functions which we specifically don’t do. Most of us are pretty anti-google overall in our company anyway. So
but it’s nearly impossible to tell the good from the bad when interviewing a company.
This is fair enough.


Exactly. And this is why I refuse to work at companies like yours.
Then good luck to you?
But you seemed to have missed the point. The images I share, are an SCA (Security Configuration Assessment)… They’re a “minimum configuration” standard. Not a standard image. Though that SCA does live as standard images in our virtualized environments for certain OSes. I’m sure if we had more physical devices out in the company-land we’d need to standardize more for images that get pushed out to them… But we don’t have enough assets out of our hands to warrant that kind of streamline.
I’m a huge proponent of Linux. Just talk to the IT people in your org… many of them will get you a way to get off the windows boat. But it has to still be done in a way that meets all the security audits/policies/whatever that the company must adhere to.
I literally go out of my way to get answers for folks who want off the windows boat. Go have a big boy adult conversation with your IT team. I’m linux only at home (to the point where my kids have NEVER used windows[especially these days with schools being chromium only]. And yes, they use arch[insert meme]), I’ve converted a bunch of our infra to linux that was historically windows for this company. If anyone wanted linux, I’d get you something that you’re happy with that met our policies. Your are outright limiting yourself to workplaces that don’t do any work in any auditable/certified field. And that seems very very short-sighted, and a quick way to limit your income in many cases.
But you do you. My company’s dev team is perfectly happy. I would know, since I also do some dev work when time allows and work with them directly, regularly. Hell most of them don’t even do work on their work issued machines at all (to the point that we’ve stopped issuing a lot of them at their request) as we have web-based VDI stuff where everything happens directly on our servers. Much easier to compile something on a machine that has scalable processors basically at a whim (nothing like 128 server cores to blast through a compile) all of those images meet our specs as far as policy goes. But if you’re looking to be that uppity annoying user, then I am also glad that you don’t work in my company. With someone like you, would be when we lose our certification(s) during the next audit period or worse… lose consumer data. You know what happens when those things happen? The company dies and you and I both don’t have jobs anymore. Though I suspect that you as the user who didn’t want to work with IT would have a harder time getting hired again (especially in my industry) than I would for fighting to keep the companies assets secure… but that one damn user (and their managers) just went rogue and refused to follow policies and restrictions put in place…
I’m a software engineer, and my department head told IT we needed Macs not because we actually do, but because they don’t support Macs so we’d be able to use the stock OS.
No you don’t. There is no tool that is Mac-only that you would need where there is no alternative. This need is a preference or more commonly referenced as a “want”… not a need. Especially modern M* macs. If you walked up to me and told me you need something… and can’t actually quantify why or how that need supersedes current policy I would also tell you no. An exception to policy needs to outweigh the cost of risk by a significant margin. A good IT team will give you answers that meet your needs and the company’s needs, but company’s needs come first.
either the company trusts me to follow best practices, or I look elsewhere
So if I gave you a link to a remote VM, and you set it up the way you want. Then I come in after the fact and check it against our SCA… you’d score even close to a reasonable score? The fact that your so resistant to working with IT from the get-go proves to me that you would fail to get anywhere close to following “best practices”. No single person can keep track and secure systems these days. It’s just not fucking possible with the 0-days that pop out of the blue seemingly every other fucking hour. The company pays me to secure their stuff. Not you. You wasting your time doing that task inefficiently and incorrectly is a waste of company resources as well. “Best practice” would be the security folks handle the security of the company no?


In the USA minimum wage will still be 7.25.
https://www.minimum-wage.org/wage-by-state
It’s not that wage now in the vast majority of states.
Edit: The actual “Average” minimum wage of a US worker is 11.33/hr. Which is a population distribution of minimum wages across all states.
I am only adding this to show the problem of treating the “federal” minimum wage as a monolithic representation of the USA. It’s not. Stop treating it as if it was.


Nah, they didn’t click the “show NSFW” toggle… Everything get’s pushed off the bottom of the page when you click that.


The adult conversation would begin with you don’t get to change things about stuff that you don’t own without permission from the owner, it’s not yours. It belongs to the company. Materially changing it in any way is a problem when you do not have permission to do so.
Most of this answer would fully depend on what operations the company actually conducts. In my case, our platform has something on the order of millions of records of background checks, growing substantially every day. SSNs, Court records, credit reports… very long list of very very identifiable information.
Even just reinstalling windows with default settings is an issue in our environment because of the stupid AI screen capture thing windows does now on consumer versions.
I’m a huge proponent of Linux. Just talk to the IT people in your org… many of them will get you a way to get off the windows boat. But it has to still be done in a way that meets all the security audits/policies/whatever that the company must adhere to. Once again, I deal a lot with compliance. If someone is found to be out of compliance willingly, we MUST take it seriously. Even ignoring the obvious risk of data leakage, just to maintain compliance with insurance liability we have to take documented measures everywhere.
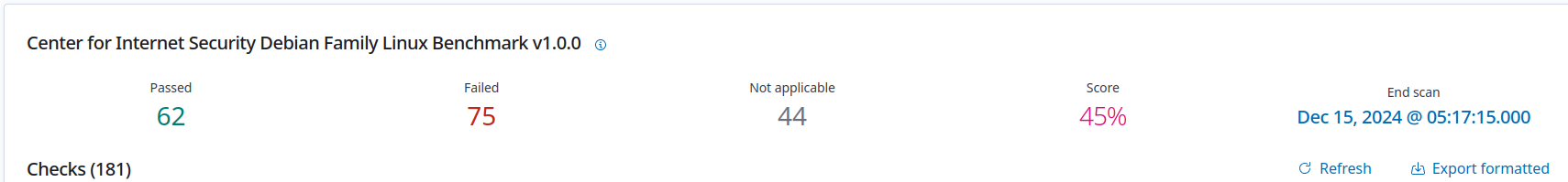
Many defaults linux installs don’t meet policy minimums, here’s an example debian box in a testing environment with default configurations from the installer. Which is benched against this standard https://www.cisecurity.org/benchmark/debian_linux.
Endpoint security would be missing for your laptop if you jumped off our infrastructure. Tracking of assets would be completely gone (eg, stolen assets. Throwing away the cost of the hardware and risking whatever data that happens to be on the device to malicious/public use). File integrity monitoring. XDR services.
Did I say that the device isn’t yours? If not, I’d like to reiterate that. It’s not yours. Obtaining root, or admin permissions on our device means we can no longer attest that the device is monitored for the entire audit period. That creates serious problems.
Edit: And who cares about downvotes? But I know it wasn’t you. It was a different lemmy.world user. Up/Downvotes are not private information.
Edit2: Typo’s and other fixings that bothered me.
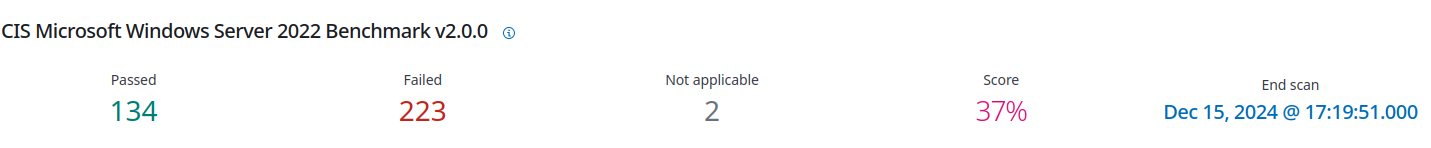
Edit3: For shits and giggles, I spun up a CLI only windows 2022 server (we use these regularly, and yes you can have windows without the normal GUI) and wanted to see what it looks like without our hardening controls on it… The answer still ends up being that all installs need configuration to make them more secure than their defaults if your company is doing anything serious.


Yeah if you did this in my company… install linux on a machine that we installed windows on. I will get you fired and hand over everything I can possibly get to HR for them to do whatever else. You don’t fuck with my infrastructure. Use your big boy adult skills and request/requisition a linux machine so that it can be done properly.
Company computers are not yours. They don’t belong to you. The people who are ultimately responsible for the company security posture don’t work for you. Sabotaging policy that’s put in place is the fastest way to get blacklisted in my industry especially since we must maintain our compliance with a number of different bodies otherwise the company is completely sunk.


that is configurable by your admin. while it was useful for you, you should probably raise that problem to your admin.


And has been available for years… Why this is news today is beyond me. I’m pretty sure I saw these cables on hak5’s site over 5 years ago.
Most of the hardware itself was free(business decommissioned) or auction wins (4.5TB of ram out of a $600 auction, selling some servers paid the whole auction off). So quite cheap in that respect. And it’s not strictly private use. Lots of functions in there to keep my business going/make it easier to track taxes/auto billing clients/email/etc. Though only typically operationally, not as an income generator itself (eg, not hosting other companies stuff so much).
And yeah, if energy was 10x more expensive (I think it was you or someone else that said $0.60 per kWh?) I’d probably rethink my situation/stance a bit.
But 3kW service is awfully low. Standard around here is 200amp service to a house (at 120v, so 24kVA service), 100amp (12kVA) if you have gas utilities handling range/heating, as A/C is heavily required where I live. My PV setup is rated 15.9kW, though caps out at 11kW on the best days. I can’t imagine living off of 3kW. My desktop uses 1/10th of that. My idle usage in my house minus the servers is ~2kW. I can see why you’re squeezing Watts. Some googling shows Italy being a country that does this… You probably are in similar situation as them where A/C isn’t really common, heating and cooking isn’t electric based, etc… Most of the year I’m not allowed to even make a fire, so I’m forced to rely on electricity.
But no SUV here… 1 hybrid sedan for this family of 4. Gas costs too much and we drive too little.
And here I am with a 5 server cluster, 2x custom servers running opnsense for redundancy (8gbps internet connection needs real horsepower for IDS/firewall/routing), and a 36 bay storage truenas node… that’s getting upgraded to 72 bay version for more drives (34 additional drives ready for install RIGHT NOW)… I see your 50 and 38 W… and raise you
This

2200-ish watts? Oh… and cooling the servers to keep them to about 75 degrees intake temp.

So really closer to 3400 watts.
Taking your numbers of 6 watts saved per drive would only save me 180w currently and 432w after I install the additional 32 drives next week. I’d still be in the 3kW territory.
…
I also have solar…

I generate (orange) enough to export (purple) a little during the day… but that’s about it… Battery (light green) usage just kills peak hours.
The electrical usage costs me about $100-110 a month in electricity after solar ($0.06 per kWh), probably closer to $150 if solar wasn’t eating up a bunch of it. Less than subscriptions to all the shit that I’m hosting for myself by a long long shot. Forget the family and other users.
Nextcloud - 5TB, google drive is $10/mo for 2TB
MSTY - AI stuff, another $10/mo subscription if you want google gemini. $20 for ChatGPT.
Minecraft - private, $5 a month minimum. Probably closer to $10 for reasonable specs to do anything with the kiddos.
Email - 1TB across all users right now, ~$5 minimum for just me, though I’m oversize for many platforms as I have everything going back to 2006 or so. So probably close to $8-10 for just me.
Private search aggregator - apparently a paid service now with the likes of kagi. $10
Home assistant - $6.50 through nobucasa.
$46-66 on this stuff alone…
Frigate… 8 cameras with corals for inferencing. God know what that cost would be. I keep 30 days of 24 hours, 6 months of detected items and 1 year of snapshots. I’m at 50TB of usage there. This probably could/should be cut down significantly, at least halved. but even 25TB is a fuck-ton of money per month on any VPS/hosted system. Ring’s plan is about half what I’m doing at $20/mo. No idea what other services would end up being. Not even sure how ring and other make money at that cost when storage is expensive otherwise.
Paperless-ngx, lubelog, grocy, gramps for organization/documentation would need a VPS service… or migrating to a non-hosted solution (so can’t really be shared easily, or shared through google docs sort of thing).
Self-hosted things like lemmy, mastodon, matrix, peertube, etc… VPS costs would be something substantial as well. And business operation stuff like my invoices, jump hosts, secure vms, etc…
And lastly, the cost of owning my own data… where no company can spy on me. Or monetize me in ads. Invidious, my own dns with custom rules for me vs the kids, etc…etc…etc… Priceless.
Then multiply the parts of the list for other users on my system (wife, both kids, father, etc…)
And of course the massive porn collection… Gotta have that on a moments notice.


Who knows how many meetings they’re involved in to constrain the crazy from senior management?
This is more than half of my job. Telling the company owners/other departments “No”. Or changing their request to something actually reasonable and selling them that they want that instead.


No, that’s an entire external service + a script.
Requires running https://github.com/Cloudbox/autoscan and that custom script.
At that point I might as well tell plex to rescan the library every x hours itself.
Edit: I forgot to add this even though I meant to
Autoscan, A-Train and Bernard are no longer actively maintained.
And that github… it no longer maintained.
Most of the internet blocks open proxies. They’re often times used in malicious attacks. Just blocking them isn’t suspicious at all.
edit: This post is also quite old. Kind of weird that you’re necro-commenting on it…