This is a very entertaining and educational article, giving insights into the methods used by thiefs to try and get access to your phone data.
I don’t like Apple but it’s great that their security is so good when it comes to this.
the methods used by thiefs to try and get access to your phone data.
It is not about accessing the data but to disassociate the current user from the phone so that the thief can reset the phone or/and it’s components for new users.
As much as I love my android phone, I have to admit Apple takes privacy and security much more seriously.
How so? A Samsung or pixel with default settings would also behave that way, possibly even more securely because it wouldn’t show the thieves your number.
I guess just anecdotally. I have a pixel 7, I’m pretty confident I could factory reset the device without 3rd party authentication. Also, from the tech channels I follow, I think I could recover my data if I forgot the password. Android has always felt more "free"and customizable, and I love it for that. But I also think that freedom allows for more exploits. It’s a trade off that’s worth it to me, personally. But if I had illegal shit to hide on my phone, I’d probably do it on an apple device.
Edit: just checked. I can completely bypass all my locked down Google Pixel settings to factory reset my phone pretty easily if I press the right keys in the right order. It would be pretty easy to steal and resell my phone.
If you do it the manual way - not unlocking the phone and doing it through settings - you can wipe it sure, but when you try to set it up it requires the prior Google account credentials to proceed. No creds, no passing go, just a shiny brick. It’s been like that for years.
Also might I recommend you take a gander at GrapheneOS for more intense security capabilities than stock.
Not sure about the latest Android version, but I managed to unlock and bypass a phone which had factory reset protection, and as far as I know a lot of vendors like Samsung have their own exploit available.
Using this you can manage to get to the settings app (while still locked, waiting for the previous owners google account) and remove the account, add your own or disable the security.
Done!
You can factory reset it easily. You can’t use it without the previous Google account credentials afterwards. You can’t reuse a stolen Pixel which has Google account logged into it.
Ding ding ding, I can confirm this. I thought it was for all devices, but I guess not.
For what it’s worth, they’re trying to fix that with Android 15. Not sure if this is one of the features they’ll also be back porting to older phones too like this article briefly touches on, but either way it sounds like if you factory reset the phone, it can’t be set up again unless they know your login: https://www.wired.com/story/android-15-theft-detection-lock/
Google says in a blog post, the company is adding four data protection features that can help keep your information locked down. The first stops your phone from being set up after a factory reset, unless the person knows your login details. “This renders a stolen device unsellable, reducing incentives for phone theft,” Google vice president Suzanne Frey writes.
Doesn’t that already exist as the Factory Reset Protection (FRP) partition?
Yeah, I’ve had to wipe pixel devices the dirty way and it prompts (requires) your credentials to continue. Maybe it’s a pixel exclusive, and others are getting it via a15?
No, its not exclusive. But FRP can be bypassed if you know the right tools.
Honestly not too familiar with that. I imagine if they’re touting this as a new thing, FRP either does something different or was lacking compared to this in some way.
Though it is Google, they could have just killed FRP in favor of this and added messaging features like they do with everything else
Edit: just checked. I can completely bypass all my locked down Google Pixel settings to factory reset my phone pretty easily if I press the right keys in the right order. It would be pretty easy to steal and resell my phone.
Mind to share what “Keys in the right order” are? I mean a link, of course, because in my experience you just can’t do that with a locked bootloader.
Enter recovery mode and choose factory reset. The specific key combination for your device may vary.
You think we’re still in 2010? It’s been a while since you need to unlock the bootloader first. And no, you can’t do it with the device locked.
This don’t work anymore, now they have frp protection which requires google authentication to the previous account after reset
AFAIK you can’t wipe the IMEI and if you report it stolen to providers they will block it from using their networks. (It will only be able to use wifi.)
Same for Samsung afaik. Pop into the bootloader and just wipe everything.
AFAIK you can’t wipe the IMEI and if you report it stolen to providers they will block it from using their networks. (It will only be able to use wifi.)
If recently upgraded an old Samsung tablet (Tab A6 from 2016) to Lineage OS and not only do you have to remove the Google Account before flashing just the TWRP to be able to just start replacing the actual OS, but there is a configuration flag that can only be changed in the stock OS logged in to that Google Account and with Dev Mode enabled to, after you replace the OS, allow the custom OS to actually work (if you don’t do it the device with the custom OS will go into a boot fail loop as soon as you restart it).
It was actually a PITA to do that upgrade of my own device because of that (I had to reinstall the old OS and log in to the old account just to toggle the “Allow OEM install” option after which I could install Lineage OS … again … without the device going into a boot fail loop on the first restart)
This is on a Samsung device that’s almost 8 years old so it would be a bit strange if they went back on it since, especially as it’s in the best interest of Samsung to make it hard for people to upgrade their devices away from the enshittified Samsung software.
The encryption on Android devices is pretty strong, as long as you use a good screen lock you should be fine. Yes they can reset you phone, but accessing your data is a whole other level.
If I had illegal shit on my phone, I wouldn’t send it to apple servers by using an iPhone. They are the first who would comply with a surpena. I’d use GrapheneOS on a Pixel and use an obvious duress pin like 1234. If entered it wipes your encryption keys and avoids restoring your data.
And if it gets stolen, it is gone and I’d get a new one. This is the cost of having proper opsec.
Edit:
But I also think that freedom allows for more exploits.
This is a common misconception called security through obscurity
Does it have to be a specific version Pixel? Just any Pixel?
Any of them still receiving security updates would be fine.
Im pretty sure u cant fuck with a device that has a locked bootloader without unlocking said bootloader which requires u know the password. And u definatly cant recover data without passcode unless u can extract the hash from whatever chip holds it (shouldn’t be possible if u have a tpm) and bruteforce it. Ur data should be encrypted and u shouldn’t be able to tamper with os without unlocking bootloader which once unlocked will wipe all device data. Might be possible if u do some dodgy power injection directly into some of the chips but thats pretty advanced stuff.
As everyone is pointing out you’re just wrong about this.
Also apple is overbearing AF. I recently had several back and forths with my IT department about an old company mac laptop I used to have. Since I had signed into my apple account once, Apple permanently tied that laptop to my account and wouldn’t allow the fucking IT department to fully wipe it.
Keep in mind also that I would have preferred to not have or use an apple account (they kind of force it on you, even asking you to login to iCloud constantly even if you’ve literally never used it once), and even though I could login to the apple account in my browser and see that the laptop wasn’t listed under my devices, IT was still locked out.
Literally the only way to fix this was giving the IT dept my apple password so they could authenticate then sign out of it. There was nothing I could do remotely about it. This is a security issue in itself. Zero reason I shouldn’t be able to use my account remotely to remove or sign that device out. Zero reason I should have to give my password to another human. Except for apple being shit.
The apple security theater is widely believed but it’s still largely theater.
Edit: before you tell me I didn’t have to give up my password, understand that I fucking know that. I could’ve driven to the office, told my employer to fuck off, had them ship the laptop, etc… all of which are things that shouldn’t be necessary. I took the least shitty option at the time. Kindly fuck off if you are so dicksloppery on apple that you can’t understand the obvious point: pretending every shit decision is about security doesn’t shield you from all criticism.
Your post details how it isn’t possible for IT professionals to wipe a Mac without the consent of the owner’s account. How is that security theater?
IT was the owner and obviously consented to their own actions.
You didn’t read the post.
You pretty much MUST use paid mobile device management tools to set up and administer company owned Apple hardware, and those tools are notoriously annoying and often just bad
MDM would have been used regardless of OS.
Read again - for most other devices there are cheap and often some free administration tools that small businesses can use. And for many devices they can just reinstall them. But for Apple devices pretty much everything is expensive or very limited.
It’s more about the fact that they didn’t have a webpage in their apple account where they could remotely log out, and the IT department had the physical computer so they had to either move to the department or give the department their personal password, which is bogus. Being able to remotely log out of the computer doesn’t seem to be that big of an ask.
I get thay the computer should remain locked if there’s no internet, but once the computer gain connectivity it should unlock if it was logged out in the user page.
I see what you’re saying. I agree that users should be able to remove device locks remotely. You can with iPhones. Hopefully that moves to all devices.
I still prefer this to not having the lock at all.
You missed the part where I had to give my password to another human.
Also, I wasn’t the owner, they are. Also, again, it makes zero sense to not allow me to sign it out remotely.
Nothing is secure about a system designed so poorly you have to give out your password. That should never be needed.
Not to mention, I never wanted or needed to sign in. I was just nagged to do so 100 times so I relented. Nothing about that means I own the device.
I’m with you that you should be able to log out remotely, but this is more of a failure in the IT department. You should have been given a PC with the apple ID already introduced, with your company mail and some password. How would they even access your PC remotely for security udpwtes if they didn’t have access to your appeal id? Right, they didn’t. So they gave a computer they didn’t have remote access to, not properly configured, and then forced you to either move or give private information.
You are absolutely incorrect. They had remote access and I watched them use it in various ways. When troubleshooting issues they would login and move my mouse and use a virtual keyboard. They could install software remotely on a schedule.
Not sure why you’re under the impression that an apple account is required for remote management. There’s probably >5 different popular third party software solutions for that
The apple sign in is an extraneous unneeded piece that once they annoy you into it, it then becomes considered a sign of ownership, which I never considered, because why would I?
You are right that IT should’ve had a way of dealing with it better, but in their defense this may have been an anti-feature (asking a user to login to iCloud, a service they’ve never used once, is not a feature) added in an update, after they issued the laptop. It’s a small company, so I don’t fault them on it as much as the trillion dollar company with the goal of inflating their iCloud metrics by forcing users to login to it.
You couldn’t remote in to type in your password?
I don’t have the type of position where that would be needed or considered appropriate. Why should I need to anyhow? A lot of people are missing the point here. Logging into a service (especially one I didn’t want or need but was harassed into doing it) should not unexpectedly be considered proof of ownership.
The scenario wasn’t that during os setup I was asked to login. And I wasn’t prompted with a warning that this could happen. What happened was every time I opened system settings for months it wanted me to login to iCloud and no matter how many times I refused it just kept asking.
Nothing is secure about a system designed so poorly you have to give out your password. That should never be needed.
You didn’t have to give out your password, in fact you never should. If the machine remains locked, that’s not your problem. Your IT department should have created an admin account on the machine for IT before handing it over to you to avoid this scenario. The IT departments incompetence is not your problem.
If you wanted to unlock it as a courtesy, then they should have offered to send the laptop to you so you could unlock it. You never ever give anyone your password, and IT should know better than to ask for it.
If someone is holding a family member at gunpoint and threatening to kill them if you don’t give up your password; you do NOT give up your password. If an evil mastermind is about to destroy the world, and it can only be saved by you telling your password to another person. You do NOT give your password. There is no valid reason to ever give your password to anyone.
You missed the point entirely. Harassing me into signing into iCloud shouldn’t mean I ever have to do anything inconvenient at all, regardless.
I wasn’t presented with a dialogue that said “login to establish device ownership”. Instead it was “login to iCloud now” dozens and dozens of times. I have never once used iCloud nor will I ever. That part alone was indefensible. But then locking the device to that account is plain stupid and reckless. There are plenty of scenarios where this fucks people worse than having to choose from a few shitty options
my account
I wasn’t the owner
You are the owner. For Apple, your IT department is the thief.
You should finish reading the part where the company owned the device.
I get this as being a bit of a hurdle, but wouldn’t a good option in hind sight be to create a separate work related apple account based on your work email? I’ve done that in the past with various companies for iPhones and MacBooks. Makes it cleaner to return the device and doesn’t compromise my personal account should they ultimately need my credentials on the non-owned-by-me device.
I eventually did do that, but apparently at the time that I was nagged into iCloud for the 1000th time I was quite annoyed and just used my personal account like an idiot.
The thing is, I never expect logging into a service to immediately lock my device to that account. But I’ve since learned not to trust Apple’s login systems for this reason. So yeah, I won’t buy any other apple devices and any work machines will use a work account for everything like that
Your “IT” could’ve literally do fresh install of MacOS. I’m not a fan of Apple, but that’s just silly.
Pretty sure that’s what they were trying to do. I know for sure that on iPhones, if you ever sign in (which I think is required), wiping the phone doesn’t matter, it’s still locked to that account somehow – a ROM chip on the board stores the account info somehow I think? I think their computers work the same way now.
On other systems, logging in means that: you’ve logged in. And you should be right: wiping the OS should always remove any login/account status. If Apple wants to provide some system like this for people worried about theft, cool, let them opt into it. But don’t force every user to.
iPhones don’t do that on their own.
She said she activated lost mode, so it’s possible/likely she made her contact info available. Asking Siri who the phone belongs to will also give up contact info, but you can change that remotely from the find my phone app.
I think - being a writer - she sort of set herself up for the interaction so she would have material. No judgment, though. It was an interesting read.
You can fairly easily factory reset phones from both. While you can report your phone as stolen and the IMEI will be blacklisted on US carriers, it would probably work fine abroad.
For iPhones, if you have Find My turned on, you can’t activate the device without the iCloud password, unless the owner removes the device from their iCloud account. Which is what the scammers are trying to get her to do here.
Sorry. When I said “both,” I meant Google and Samsung. Apple definitely has better security, ocassionally to an annoying extent.
As far as I know factory resetting an android phone is relatively easy without having access to the device. But it’s been a while since I’ve looked I hti that.
Security yes, but privacy not so much…
If you’re talking about a stock Android OS on anything other than a Pixel, iOS wins in both regards. Stock on a Pixel, I don’t know that Apple is more secure, but if you’re installing apps via Google Play that use Google Play Services, iOS is certainly more private. Vs GrapheneOS on a Pixel, iOS is less private by far.
Better than bad is not good.
Better than bad is still “better.”
It is if it’s LOG!

Apple is more secure… iOS is certainly more private.
False, anti-libre software bans us from proving it’s claims.
You think that Google Play Services is FOSS? Or that the version of Android on Samsung phones (as well as of most other Android phone manufacturers), including all baked in software, is FOSS?
Where did I say that?
And when you’re comparing two closed source options, there are techniques available to evaluate them. Based off the results of people who have published their results from using these techniques, Apple is not as private as they claim. This is most egregious when it comes to first party apps, which is concerning. However, when it comes to using any non-Apple app, they’re much better than Google is when using any non-Google app.
There’s enough overlap in skillset that pretty much anyone performing those evaluations will likely find it trivial to configure Android to be privacy-respecting - i.e., by using GrapheneOS on a Pixel or some other custom ROM - but most users are not going to do that.
And if someone is not going to do that, Android is worse for their privacy.
It doesn’t make sense to say “iPhones are worse at respecting user privacy than Android phones” when by default and in practice for most people, the opposite is true. What we should be saying is “iPhones are better at respecting privacy by default, but if privacy is important to you, the best option is to put in a bit of extra work and install GrapheneOS on a Pixel.”
Compared to any android phone the privacy is substantially better. Apple is in the business of selling overpriced phones. Google is in the data collection business.
The issue here is that while baseline apple is more secure than baseline android, a user with knowledge or a guide can improve the android security by a lot, whereas the apple baseline is also the ceiling. There’s stuff you can do with iPhones but if you don’t trust apple, you are kind of fucked.
Android people that mention security won’t be using a stock phone from the store, they will have disabled stuff, enables alternative stuff, or even installed a completely new android based OS, and this can’t be done with iPhone or iOS.
True. But for 99% of people baseline is what they use. Windows can be made very secure by experts but the fact is 99% of people just use windows as is.
100% agree, just take into account that most people you encounter on lemmy, specially on posts about security, are in that 1% that tweak stuff and if you throw blanked statements they will think you are talking to them specifically.
Fair. And I see it lol. My inbox is full of people who want to argue with me.
The issue here is that while baseline apple is more secure than baseline android, a user with knowledge or a guide can improve the android security by a lot, whereas the apple baseline is also the ceiling.
Not true. iPhone can be locked down much more than it is out of the box, and it’s as simple as changing one setting. Lockdown mode, it significantly tightens down security of iOS at the cost of some convenience. It is not recommended for the average user, only if you expect to be targeted by highly sophisticated attackers.
There’s stuff you can do with iPhones but if you don’t trust apple, you are kind of fucked.
That is always the case. If you don’t trust the company that made the hardware, there is nothing you can do. Unless you’ve got your own chip fab, there is always a level of trust involved.
It’s not really about the hardware, is it? The option you mentioned won’t enable an alternative app store, it won’t enable access to android app emulators (which would be a huge boom in the open source app offering). The level of trust iPhone users give to appeal is wildly higher that what android users that tweak their phones give the manufacturers. It is what it is, but don’t delude yourself in thinking that it’s about what they do in the kernel level, it’s about the fact that they store tons of sensitive data in their american servers and that they have an obligation to share that data with the country, and as someone from Europe that doesn’t sit well with me.
It’s not really about the hardware, is it?
It’s about everything, that’s the point
The option you mentioned won’t enable an alternative app store, it won’t enable access to android app emulators
I don’t see how that would help in any way to secure the device if you don’t trust Apple.
The level of trust iPhone users give to appeal is wildly higher that what android users that tweak their phones give the manufacturers.
You either trust a company or you don’t. There is no grey area. If you don’t control the whole thing, you don’t control anything at all. A custom ROM on your Android device is not going to do anything to prevent a firmware or hardware level backdoor. Your custom ROM doesn’t improve security, on the contrary. If you unlock the bootloader you break the chain of trust and all bets are off.
If you aren’t using the iOS lockdown mode, it’s not really that much more private. Most stuff is still not encrypted in iCloud without that on, and apps can still track much of what you do, and Apple has their own ad networks.
Edit: has any of the downvoters actually read Apple’s (public!) security architecture documents?
Anti-libre software, iOS, bans us from proving its claims. Stop paying Apple to pre-infect our devices and spy on us too.
My devices need libre software, not a business.
You are preaching to the choir.
When it comes to privacy: GrapheneOS > iOS > android with Google.
Android itself is good. It’s just android with Google that’s the problem. (Aka 99.999% of all android phones sold outside of China)
iOS > android with Google
They ban us from proving this. Both malware, anti-libre software, ban us from proving it’s claims.
Why do you keep posting the same thing over and over?
Their posts won’t change much, so obviously our replies don’t either.
Anti-libre software, iOS, bans us from removing malicous source code. Don’t let this malware infect you.
What are you talking about, it’s literally the same thing on Android. Also why the shilling out of nowhere?
they love bricked phones because it means one less for a secondhand market
Lol you’re basically gaslighting yourself
Apple has the benefit of making everything themselves, down to the secure enclave processors and, as of some time also, the processor as a whole. They get to design their hardware, OS, software, ecosystem, all around security and it all plays together nicely.
If you control everything, you can do whatever you want with it. Android phones being more of a mixed bag of different vendors making different parts of the phone, including the software components, makes this interplay much more difficult. It usually takes android quite some time before they catch up on the latest security concepts.
It usually takes android quite some time before they catch up on the latest security concepts.
Android exploits are considered more valuable and expensive because they’re harder to find. I don’t know where you are getting this information other than thinking it sounds correct in your head.
Don’t think Apple security is much better. I’ve read news before about insiders that will unlock stolen phones. They work closely with the criminals and it’s a more “professional” operation. Probably it’s not as easy as doing it for an android but having an iPhone and thinking that if someone steals yours it will just become a paperweight is wrong. Sadly
Man, the last threat the author received was absolutely BEGGING for the navy seal copypasta lololol
But give them one of the more obscure versions so they don’t immediately realize what it is.
What’s this you’ve said to me, my good friend? Ill have you know I graduated top of my class in conflict resolution, and Ive been involved in numerous friendly discussions, and I have over 300 confirmed friends. I am trained in polite discussions and I’m the top mediator in the entire neighborhood. You are worth more to me than just another target. I hope we will come to have a friendship never before seen on this Earth. Don’t you think you might be hurting someone’s feelings saying that over the internet? Think about it, my friend. As we speak I am contacting my good friends across the USA and your P.O. box is being traced right now so you better prepare for the greeting cards, friend. The greeting cards that help you with your hate. You should look forward to it, friend. I can be anywhere, anytime for you, and I can calm you in over seven hundred ways, and that’s just with my chess set. Not only am I extensively trained in conflict resolution, but I have access to the entire group of my friends and I will use them to their full extent to start our new friendship. If only you could have known what kindness and love your little comment was about to bring you, maybe you would have reached out sooner. But you couldn’t, you didn’t, and now we get to start a new friendship, you unique person. I will give you gifts and you might have a hard time keeping up. You’re finally living, friend.
Hadn’t seen that one before. That’s a good one, lol
Honestly I’m scared of when these people figure out they can use llms to make their texts look like less obvious scams
Often scammers don’t want to make it less obvious. If it’s obvious and the mark falls for it, it’s a good indicator they’re on the hook and will fall for more. It’s to filter out the less gullible so the scammer doesn’t waste their time. Probably not the case with this situation specifically, but it holds true in general with scams.
True. But also true is that a majority of scammers are simply not smart and/or English is not their native language. A phishing email/text that might look good to them, can look really bad to others.
But still, people still fall for the obvious phishing attacks. AI is going to make the phishing appear more legit.
Probably not the case with this situation specifically
Yeah :( High-value item already in hand, never a need to guide somebody which store to buy the giftcard at or what to say to the bank teller…
On a similar note, a reason why you shouldn’t respond to spam/scam texts because it basically verifies you as an active phone number. Why waste man/bot power texting numbers that may or may not exist when a majority of your texts will at least be seen by a human which will probably boost their chance
It’s why I tell my friends not to respond even tho some of their responses are really funny
Some smarter ones I see usually range between 2-7 lines of text usually written as a time sensitive question that will affect the totally real persons social or work like
One of my favorite ones was about 5 lines of text that was posed as a date
It was like “Hey Kayla it’s Mike, some short sob story about dating life, hope our first date goes well, then nonsense about dating with an address thrown in
However after the 5 lines it was in Arabic or some similar flowy characters and when I translated it continued “mikes” story about where he was from and how oh so sad his life was
Tldr totally fishing for a pity “sorry wrong number” to see if my phone number would be seen by human
I’m confused, in the article he said it was a brick to whoever has his stolen phone. How did they get his phone number to send him text messages? Did they crack the passcode and needed the iCloud password?
I think when you remotely wipe the phone you can make it show a message with your phone number, in case you’re actually a honest person that found the phone instead of a thief.
In the response posts to the article someone said they got the icloud address via reset request which you can use in iMessage.
Not an i phone person so i can’t verify but thought id pass that along.
That’s interesting, never thought of that as an attack vector.
The phone itself (by IMEI) is a brick. The sim and same phone number were assigned to a new phone and they texted that number
Issue here is the iPhone 14 USA models are all e-Sim. They don’t have sim cards to remove. The article says it was a iPhone 14 Pro.
Typically if you report the phone stolen to your provider they blacklist the IMEI which gets shared with other providers so the phone can no longer be used. I was unclear on this part but a new e-sim can be provided for the new phone, and the old sim banned or the old one transferred. Regardless, the old phone will still show the IMEI/sim/phone number, which is how they got that to text them
IMEI doesn’t mean shit, you can easily change it and no one really blacklists them. The iPhone is bricked on a hardware level through iCloud.
So they took the SIM card out and got the phone number from that? I guess I didn’t realize you could do that.
Yes, it’s the SIM card that carries your number and may also carry data on your contacts if you save it there.
They almost definitely got this info by simply having the IMEI, which is printed on the back and can definitely be accessed in whatever Apple calls their service mode though.
And has had a PIN lock from the start. Doesn’t help if you leave it as 1234, though.
How would you set that pin on a SIM card in an iPhone?
On iOS:
Settings > cellular > SIM PIN
Thanks!
True, although this option loses popularity over the years.
And you can use that phone number to find their full name and address.
*her
Whoa that was a wild ride, worth the read. It’s a sad market that exists, great to see Apple’s privacy and security at work (as an Android user even).
I’m not a big fan of iphones or a lot of stuff apple does anymore, but I’m seriously considering moving back to Apple since Google keeps seeming like a worse and worse option (and I’m just not ready to ready to move to some firmware-hacked or otherwise degooglefied Android system). Yesterday’s article about their privacy lead getting fired/quitting and not replaced is just the latest nail.
I’m saying this as a lifetime Linux user and decently tech competent person who knows all about the different android roms: if you’re considering it, switch to ios as soon as you can. Buy the phone outright from apple, no financing or plan.
Someone’s going to sell your phone on the black market
is my favorite
Oh no! Then I won’t have my phone anymore!
Wait just a second…
Why doesn’t anything this interesting happen to me!
As the author found out, these phones end up in Shenzhen. You can buy these burnt logic boards on the cheap and lots do just for testing. Check out Strange Parts on YT, he has soldered lots of boards and shows they sell them in bins. The grey market is the only place for them.
Also, for those that aren’t familiar with how Apple’s encryption works. The OS creates a key pair when you create your account, fully encrypting the contents. The contents become garbage if the key pair cannot be matched. This means even if you don’t remotely wipe the contents, the data they try to get from say recovery software or whatever, cannot be read. It’s of course good to wipe it remotely in case they guess your PIN, but if they can’t, then the data is gone forever. From a technical perspective, it’s actually pretty cool.
Android uses similar storage encryption (and you can activate encryption for an SD card if you have sensitive data on it), the encryption key is protected by a TPM or Secure Element chip or by ARM TrustZone or equivalent, it checks that the OS is unmodified before booting and the chip only gives the key to the CPU if the user enters the correct PIN
The article does not mention reporting it to the police. I get that 99.99% of the time, nothing will come of it, but that’s something I would immediately do. Maybe I just don’t get the rich aspect of going out and buying the newest latest model right away and forgetting about the stolen phone, even if it is theoretically still in the reach of police forces.
What are the police going to do about your phone?
“Yup. It sure is gone now. Have a nice day.”
“it’s a civil issue”
“It’s a shame about the Credence”
99.99% seems optimistic. You’re gonna have to buy a new phone regardless, if it’s stolen then it’s gone. You can either wait a few days and then buy a new one, or you can just buy it right away
It’s literally a waste of my time to report it to the police. Plus I ain’t speaking to the police unless I’m under arrest and even then it’s to say no comment.
Sure if I see someone get murdered or a something serious then sure I’ll speak, but generally the police can get to fuck. They’re not friends and I’ve only ever had bad interactions with them.
Why would anyone ever interact with the police unless it was absolutely required? They’re not gonna care about your phone, and they might shoot your dog in the process.
ACAB
You should never ever ever purposefully attempt to interact with the police.
“Hello, police? I’d like to report my phone as stolen.”
“…Likely story. How are you on the phone with us right now, criminal scum?!”
criminal scum.
This is when the cops roll up and shoot your guar
this sounds like a joke but it isn’t. cops have killed people who called them for help
Stop resisting!
yeah, let’s invite armed thugs to your location, then piss them off by asking them to help find your precious. unless it’s for insurance purposes, leave police out. if you have 1 problem, and call police, now you have 2.
No joke my dad found a phone while on public trans on his way home from work and 2 hours later the cops showed up knocked and asked for the phone.
Owner choose not to press charges.
I live in a major US city. Who knew!
There’s no point in reporting this to the police in the US. They literally do not care and will not do anything about it.
As someone who’s experienced the same thing, some of the messages I received were shockingly well written.
The fake “find my” site they tried to use to convince me to log into my iCloud account was wildly convincing, if not for the index.php at the end of the URL - something Apple would never configure for service endpoints.
They continued to try - but never threatening. However I never engaged and eventually they just stopped trying.
yeah and the said part is most people without the tech background would never notice the index.php in the URL, or care.
This made me realize, as an android user, I have no idea what I’m supposed to do if someone steals my phone.
They have the same system. The phone is tied to your account and you can track, lock and erase it remotely with Google’s Find My Device.
Luckily I’ve only had to use “find my device” whenever my phone decides to catch-up with the TV remotes under the couch cushions
We have a black coffee table and sometimes it’s just on the coffee table and I’m like “Jesus fucking Christ what is wrong with you.”. In fairness to me, it’s summer, I keep the shades drawn, keeps the temps down.
Except you can more easily wipe the os at a low level and fully factory reset the device. That’s not possible with iPhones.
Afaik, that changed a while ago. Nowadays, it should still ask for the google account of the most recent owner.
yeah, factory reset protection, it wipes the user data, but will refuse to fully finish setting up the the os after the reset until the google acct is verified…
Funny thing, even if you do that you can be prevented from initializing the device. You get a “this phone was reset in an unusual way, sign in to the original account used for setup” message the may or not hint at an email address. I’ve got a stack of them on my desk from former employees that I’m trying to get back into. Pain in the ass for business, good for consumers.
You can’t do that on modern phones with locked bootloader. This is the reason why manufacturers who allow bootloader unlock still don’t ship phones with bootloader unlocked by default.
Luckily google keeps track of your every movement by default 🙂
Yeah and apple doesn’t…
?
Google has the same thing
hopefully you have it locked so they just wipe the data. and then you buy a new phone.
Encrypt it with a strong password in the first place…
Uhg! It’s outta control.
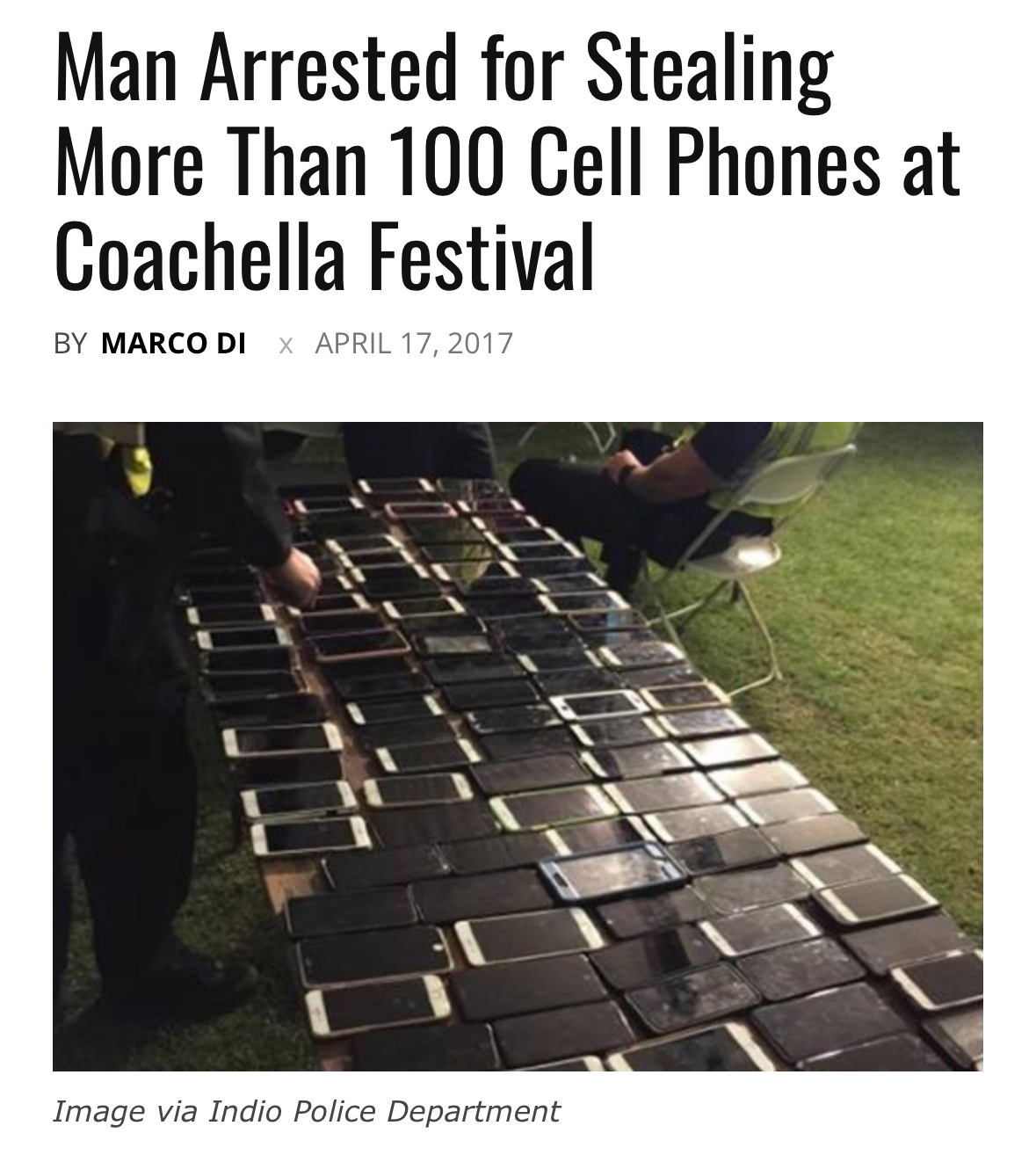
Does anybody have ideas for an anti-pick-pocketing solution they’d like to share? I might have to start a community for it. Or maybe you know some forums where designers who may be interested might be hanging out.
Requirements:
- retrofit almost any front pants/shorts pocket
- allow for near instant access (allowing for e.g. snapping a photo before the moment passes)
- one-handed access
- mechanical/passive: non-battery operated or fails in “unlocked” mode
- if not locked to owner’s hand (or say a finger-worn key), makes removal feel obvious
- automatically resets (resilient & inebriated person approved)
- ideally works with any phone case
- relatively inexpensive, and potentially even open source and/or 3D printable
Lately been imagining something like this, kinda… not really, and with only 2-3 fins:

so you gotta pull your phone out in a way that stretches the pocket to max width and one fin noticeably rubs against your leg.
Doesn’t meet all the requirements but also thought about a long and wide strip of cloth sewn at the bottom of a pocket that you could tuck into your waistband.
Edit: aware of one existing solution but not a huge fan

Oh my god, wallet chains are going to make a comeback, but for phones this time.
Next: pants sagging so much I can see 4" of crack
ahh the 00s
Honestly you can get a lot done just by wrapping a rubber band or two around your phone, it’ll kinda catch and hold in your pocket and make it more notable if someone tries to pull it out. Works for your wallet too, and all without building a whole ass mousetrap for your pocket.
Oh dude great idea! Also if you did it with hair ties you could keep extra hair ties that way! (Albeit stretched out)
Velcro sewn to just inside the top of your pocket, so sticking a hand in your pocket makes a loud noise and you can feel it, for any pickpocket to separate the velcro.
Mouse trap phone case. It fulfills almost none of the requirements, but it’ll be satisfying when a thief gets snapped.
Decoy phone that is actually a tazer, real phone in underwear.
Don’t get them mixed up…
Yeah it’s great the first time it works but then you have to spend 5 minutes looking for and assembling all the bits and pieces to set it up again.
Also might wanna try to just bring a cheap phone you wouldn’t mind to lose just in case you do manage to lose it. Back up your data so if it does go missing you’ll have the memories.
Not a bad strategy at all.
Still, hate to negotiate with terrorists. And bring home potato photos. Instead of $developing-nation-per-capita-GDP phone quality photos.
Which of course means the thieves will still be tempted! If anti-pickpocketing strategy becomes too successful, they’ll move to violent means, then a cheap phone will be a must.
Well phones are generally pretty good for taking pictures and videos. A pixel 4 or something is a pretty decent phone for example.
That’s a great idea! Thank ve thought about carrying a decoy wallet before, but a decoy phone is also a great idea
Cargo shirts obviously. Those zippers have a purpose!
I use a fanny pack at large events.
Many have hidden zippers for wallet and phone, and its in front of you so its hard to steal from.
Thanks, phone theft is rampant in nightclubs as well and would be great to solve for the pocket problem.
Do like these guys (who I think spend a lot of money on marketing):

I got a cheap one from Amazon.
A key thing a look for are those little nylon pulls on the zipper handles. You can always add them to a zipper as well.
You can loop the pulls through each other to make it harder to open a zipper. I do this for backpacks since they’re behind me. This is more of a deterrent than a lock though.
I’ll send a pic after work to describe it. (Although there are actual products but I am cheap).
Just a phone case with a retractable tether would work fine. Put it in your pocket. Tether is out of the way, completely invisible. Pull it out, tether extends enough to use it, and reteacs when you’re done. With a clip or strap, you can attach it to just about any outfit easily enough.
Realistically, if you have to have a phone somewhere like this where pickpocketing is likely, id suggest either a cheap phone you can lose, or keeping your phone in your hand/a hand on it in your pocket.
I also fucking hate Apple, with the same seething rage that redhats hate Windows, and I too must admit this is shockingly effective security.
Is it though? The author of this article knows what they’re doing, but a regular person would probably not be as relaxed with some of the threats. I didn’t see this in the article, how does the thief have the ability to contact the victim?
when you end up with someones iphone (or mac or ipad or whatever) and you want to wipe it, the computer needs you to enter the credentials of their icloud account. it tells you whose icloud credentials you need, just like having the username entered but asking for the password.
icloud usernames can be used to send imessages to the owner of the account, like you could call someone with their phone number or IM them with their screen name.
the idea is that a thief ought not be able to just wipe and repurpose a stolen device but a gifted or purchased device should provide a method to contact the person so the new owner can wipe it.
it works pretty good because if a local thief contacts you trying to get you to let them have your device you can call the cops and you already have a line of contact with the person who has the stolen goods so the police can’t even say “yeah whatever, we don’t care, its gone heres some tissues” and it’s very easy to track them down. it also works great if you buy a used device from someone and they won’t clear it to wipe because if you have a transaction record like on ebay or facebook marketplace or something you can also go to the authorities and say “hey, i bought this, here’s proof, and the person i bought it from won’t relinquish ownership of it”
what happens now is thieves ship a bunch of phones off to somewhere outside the juristiction of the victims governments and then they break em down to be sold for parts. now there’s nothing the authorities can do and the thieves accomplices can try to socially engineer the victims into giving them what they want with impunity.
that’s whats happening in the linked article, the victim is being harassed by whoever bought their phone from a thief.
Sure. My point was that exposing someone to scams like social engineering is really really bad and far less desirable than keeping an open line of communication for a purchase
Eh, I think the alternative is worse. If you could wipe stolen phones with impunity they’d be even more of a theft and fraud target than they already are and if they were just locked down with no way out then it’d be more wasteful than it already is.
my experience with iCloud is pretty bad. I worked in a startup at some point which was giving Macs to employees and sort of expected them to figure it out. We had a few people quit and that’s when we figured out that the macs became shiny useless things since we didn’t have access to wipe the associated account and Apple didn’t help in any way. So, from my experience, this is a horrible “feature”.
Now i find out that it’s even worse and it gives 3rd parties means to harass you… I really think that avoiding theft comes at a far to high a price
lol that sucks for the company but that’s what you get when you don’t use some kind of MDM scheme to retain control over assets. It’s especially costly to learn this lesson with Macs though.
I repair and resell scrap computers and if you’re able to prove ownership or have a business that repairs or otherwise handles Mac computers the people at the Apple Store will disable the lock for you. They take down your name and tax id and stuff though, so there’s some accountability, and it’s not easy to get to that point when you look like a greaseball and aren’t a member of apples authorized repair program. Ask me how I know lol.
Tbh it’s no different than a Chromebook or windows laptop that shows the owners email based username (in the case of windows computers with Microsoft ids it shows the users real name as well!) at the login screen, except that you can’t wipe it and resell it.
Oh it could be better for sure. But he’s got access to all the messages and data, getting a number at that point is probably trivial.
I don’t ‘do’ smartphones at all, I think they’re an expensive trap – but if you have an iPhone and it gets stolen, can’t you call up Apple and have them brick it, so it can’t be used at all anymore? I’d think that would be what you’d ultimately have to do if you can’t get it back.
Removed by mod
Removed by mod
Yes. In the article she states she did exactly this.
If the guy you’re responding to could actually read, he’d be really upset.
You can bite me too, jackass.
Lol
Dude why even comment?
Removed by mod
I mean, they’re extremely useful and cheap, if you buy the right one.
No, they’re not, they’re just a way for corporations to collect data from you and for the government to track you everywhere you go, and you’re footing the bill for all that.
They’re not useful? I’m literally using one right now in a way that can’t be done on a dumb phone. Look, I love dumb phones, and I would actually have one if my lifestyle allowed it, but I get so much value out of my smart phone it’s just not practical to use a less capable device.
They’re a trap, and you’re caught in it, and by the way the vast majority of people who have them just use them as an amusement device and a time-waster. Meanwhile the telecoms and app companies are invading their privacy and sucking down all their data.
You know we can have one without the other if we campaign to make their invasion of our privacy illegal, right?
You sound fun at (key signing) parties
Bugger off loser